FlexSpy Application Analysis
Background
On 04/22/2017 FlexiDie released source code and binaries for FlexiSpy’s mobile spyware program. Being the good reverse engineer that I am, my analysis is below. The IOC section is intended for other reverse engineers and antivirus vendors. General Overview is intended for journalists. I will release a detailed technical teardown in a day or two.
IOCs
The URL and Strings section below are intended for AV companies. This can be used for identification purposes. When I have more time I’ll try knock out some yara rules.
URLs
http://58.137.119.229/RainbowCore/
(found in com.vvt.phoenix.prot.test.CSMTest)
"http://trkps.com/m.php?lat=%f&long=%f&t=%s&i=%s&z=5"
(found in source//location_capture/tests/location_capture_tests/src/com/vvt/locationcapture/tests/Location_capture_testsActivity.java:)
Another IP address was found commented out in the code base
//private String mUrl = "http://202.176.88.55:8880/
Strings
The following strings were found in the source code leak, filename: /source/phoenix/test/phoenix_demo/src/demo/vvt/phoenix/PhoenixDemoActivity.java:
"/sdcard/pdemo/";
"http://58.137.119.229/RainbowCore/";
"http://192.168.2.116/RainbowCore/";
"gateway/unstructured";
/sdcard/data/data/com.vvt.im"
General Overview
This section is intended for journalists and those who want a minimized technical writeup of the spyware. This analysis was done via briefly reverse engineering the two android applications and examining the leaked source code. The source code is for version 1.00.1, while the android applications are at versions 2.24.3 and 2.25.1. The versioning is important because 1.00.1 has the capability to only monitor one instant message application, while the 2.24.3 version monitors over one dozen popular instant message clients. Please note that this blog post represents a few hours of analysis and there might be more functionality within the code base.
The application is intended to be installed on a mobile device. If the device is rooted, a series of steps occur that ensure the spyware can persist on the victim’s device. At the time of this writing I have not found if or how the spyware can root a non rooted device.
The malware supports a variety of commands which include but are not limited to: audio recordings, video recordings, phone call recordings (incoming and outgoing calls) wiping data on the mobile device, SMS interception, monitoring for keywords in SMS messages, monitoring camera photos, contacts, calendar info, geolocation tracking, gmail app messages, and a group of plugins designed to monitor particular instant message applications.
All these capabilities are possible because the mobile application requests numerous permissions off the device. But it is my understanding that the monitoring of other applications: whatsapp, snapchat etc, can not be done unless the mobile device is rooted
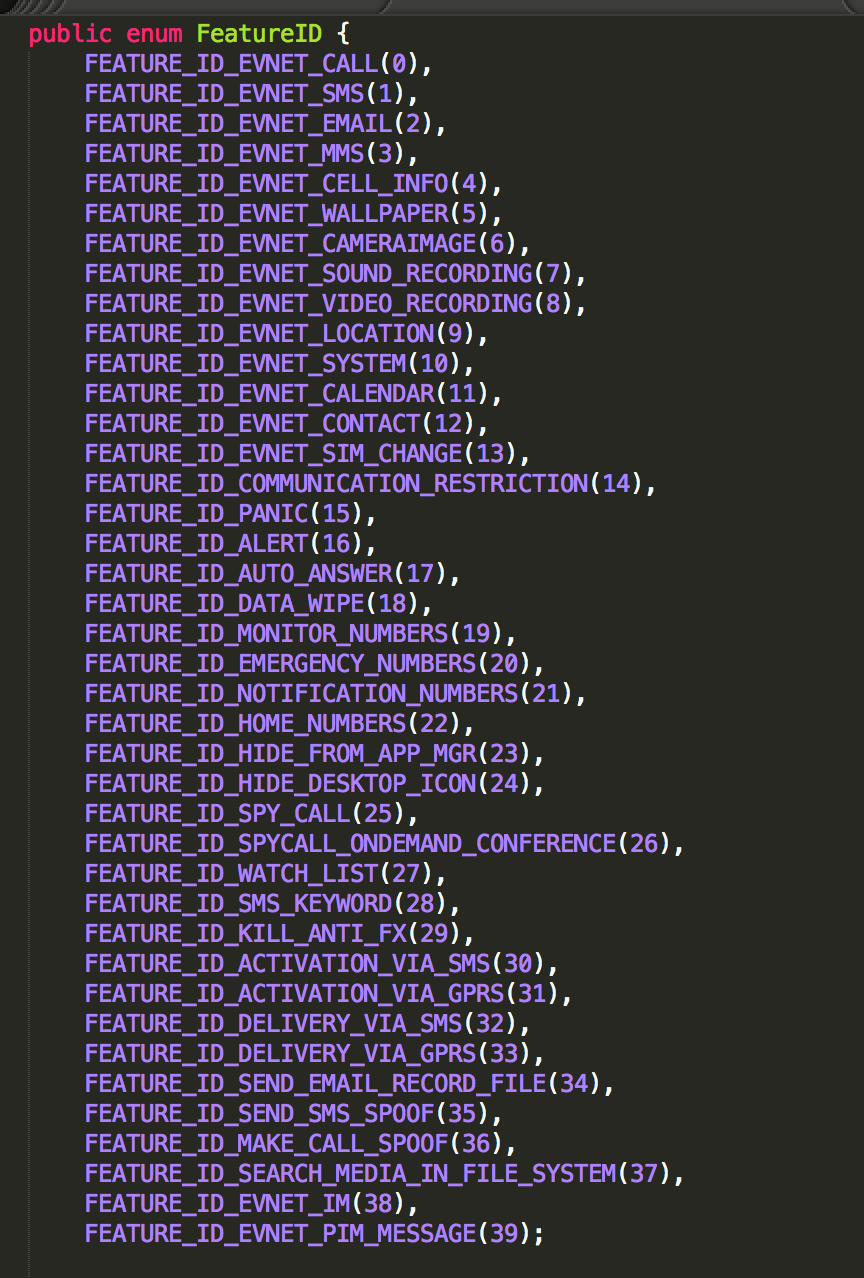
Application Monitoring
The APK has a module system that allows for the extraction of sensitive information for a variety of applications. Normally the application data for these apps are protected, but if the phone can be rooted, the spyware has the ability to grab sensitive information for any application.
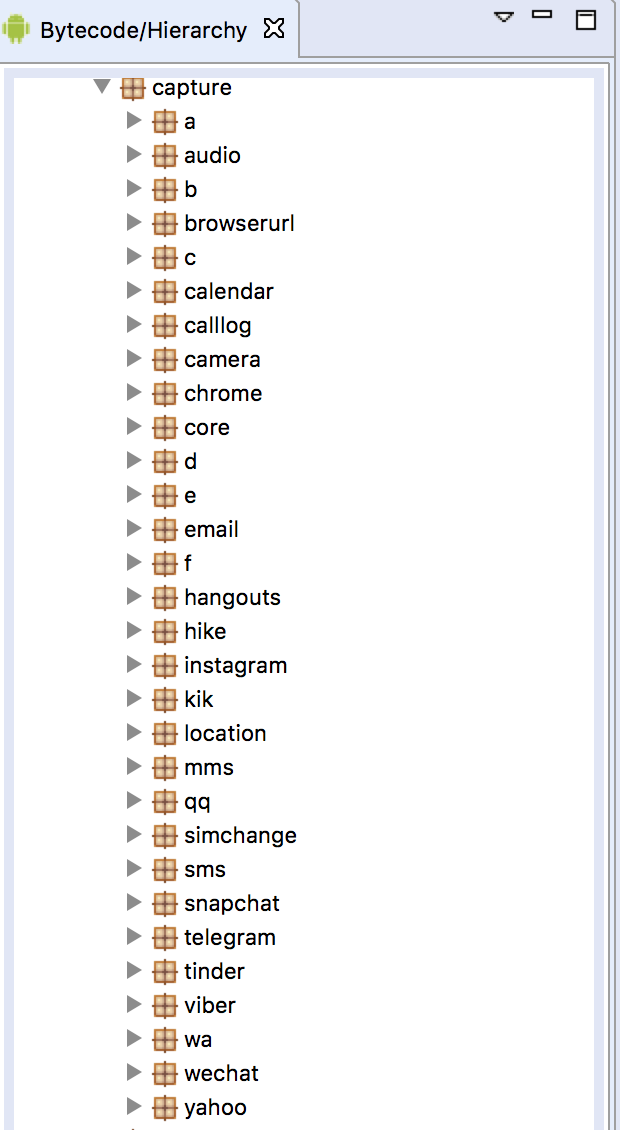
Whats App
Has the ability to grab all the private whats app files on the mobile device. Whether this includes private messages and attachments needs to be tested.
Snapchat
References in code to grabbing the internal snapchat files. The phone would need to be rooted for this to work
public static String a(String arg10, String arg11) {
String v0;
String v1 = null;
String[] v3 = new String[]{String.format("%s/%s/%s/%s", "/data/data", "com.snapchat.android", arg10, arg11), String.format("%s/%s/%s/%s", "/dbdata/databases", "com.snapchat.android", arg10, arg11)};
int v4 = v3.length;
int v2 = 0;
while(true) {
if(v2 < v4) {
v0 = v3[v2];
if(ShellUtil.b(v0)) {
}
else {
++v2;
continue;
}
}
else {
return v1;
}
return v0;
}
return v1;
Coming Soon
On my flight back from Bsides Nashville, I’ll finish reverse engineering the APKs and provide a deep technical dive into them.
 Cyber Merchants of Death
Cyber Merchants of Death